“Remote-Control” Data Anywhere in the World

How did we get here?
Remote-control data is paramount post-pandemic. It’s possible that as many as 80 million workers will continue as ‘remote,’ or at least a hybrid WFH/work-at-office arrangement. Post-pandemic legal operations are negatively impacted as well. https://www.youtube.com/watch?v=4ZxqXg5ZM6g&t=54s
COVID-19 introduces an exponential increase of data risk
With the expanded remote workforce, more activity takes place outside the firewall, more data exchanges outside the firewall and structured data converts to ‘unstructured data, and that data is the target for hackers. According to Jim Boehm and James Kaplan of McKinsey, and Nathan Sportsman of Praetorian: “A broad shift toward work-from-home arrangements has amplified long-standing cybersecurity challenges. It has opened multiple vectors for cyberattacks.”
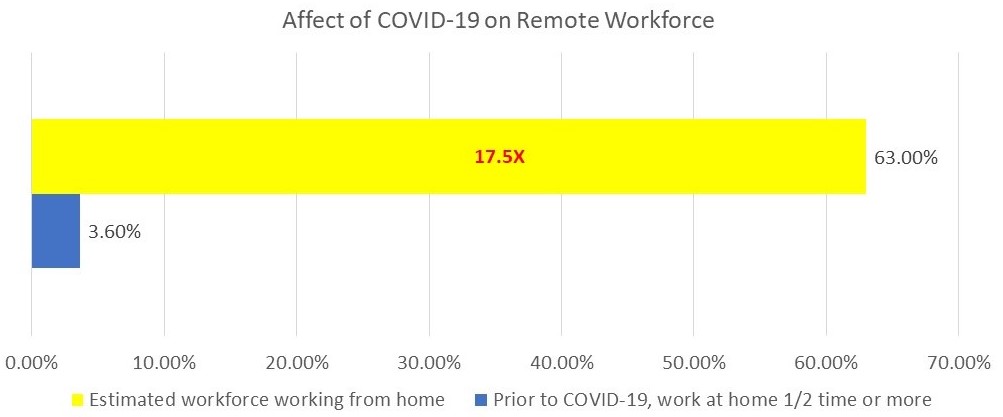
According to Global Workplace Analytics, only 3.6% of the employee workforce works at home half-time or more. Since 56% of the workforce had favorable work-at-home conditions prior to the pandemic, it is estimated that at least that many are working from home at this time. Estimates indicate an increase of remote workers to almost 80 million, a 1700% increase
As an indirect reference to the book by Susan M. Campbell, “From Chaos to Confidence,” one expert noted –
In the context of a much larger distributed workforce, data security necessary for data privacy is more difficult as the data is now spread to nodes where the security perimeter is questionable. And collecting data necessary for litigation and regulatory compliance is much more difficult.
Enabling Remote-Control Data
Heureka enables data classification of PII/PHI and file actions based on InfoGov principles and data collection. Data intelligence and insight are immediately available when sensitive data is at risk.
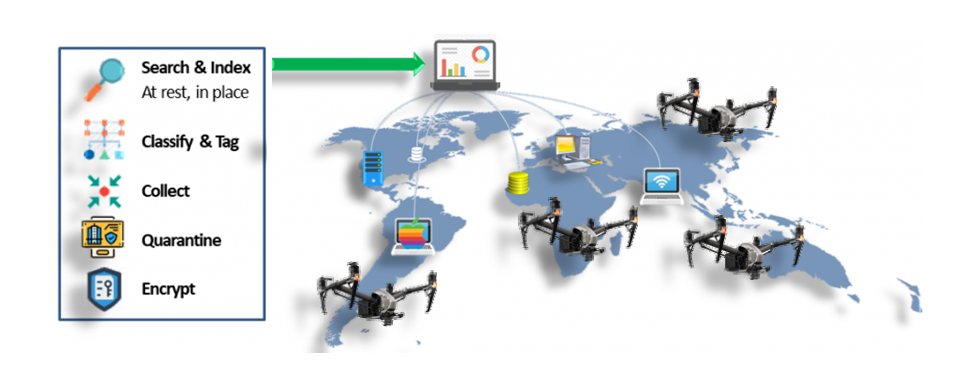
Heureka’s Indexing and Classification & Tagging capabilities afford benefits to include:
- Disciplined, enterprise-wide file identification and classification of PIi/PHI/PCI
- Response data for cybersecurity events and privacy requests (SAR’s/DSAR’s)
- Global classifications to inform data-driven workflows, i.e., DLP
- Analysis of data in-place, at rest without copying and/or moving data
- Litigation and matter preparation and Proportionality
- Defensible data